Explain hardwired
hardwired Technical Terms
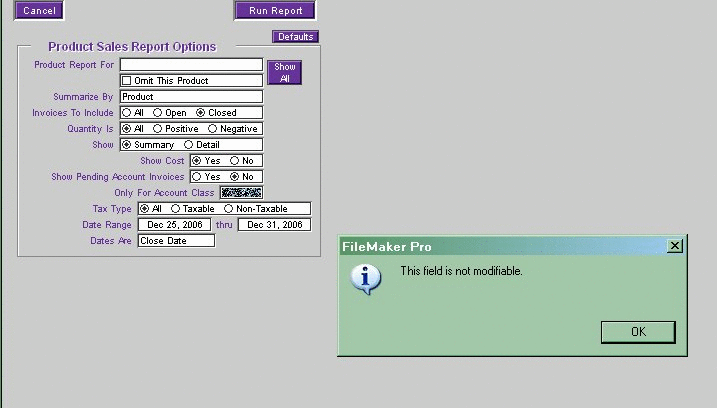
hardwired: adj. 1. In software, syn. for {hardcoded}. 2. By extension, anything that is not modifiable, especially in the sense of customizable to one's particular needs or tastes.
Expose has the X nature

has the X nature Technical Terms
has the X nature: [seems to derive from Zen Buddhist koans of the form "Does an X have the Buddha-nature?"] adj. Common hacker construction for `is an X', used for humorous emphasis. "Anyone who can't even use a program with on-screen help embedded in it truly has the {loser} nature!" See also {the X that can be Y is not the true X}.
Explain hash bucket
hash bucket Technical Terms
hash bucket: n. A notional receptacle into which more than one thing accessed by the same key or short code might be dropped. When you look up a name in the phone book (for example), you typically hash it by extracting its first letter; the hash buckets are the alphabetically ordered letter sections. This is used as techspeak with respect to code that uses actual hash functions; in jargon, it is used for human associative memory as well. Thus, two things `in the same hash bucket' may be confused with each other. "If you hash English words only by length, you get too many common grammar words in the first couple of hash buckets." Compare {hash collision}.
Explain hash collision
hash collision Technical Terms
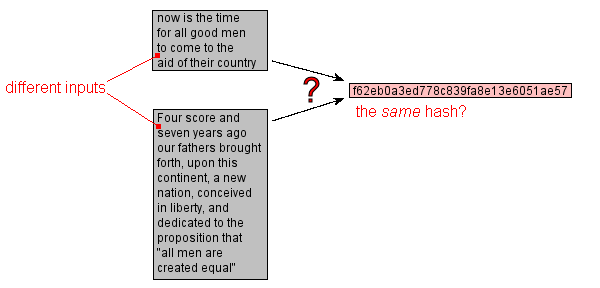
hash collision: [from the technical usage] n. (var. `hash clash') When used of people, signifies a confusion in associative memory or imagination, especially a persistent one (see {thinko}). True story: One of us [ESR] was once on the phone with a friend about to move out to Berkeley. When asked what he expected Berkeley to be like, the friend replied: "Well, I have this mental picture of naked women throwing Molotov cocktails, but I think that's just a collision in my hash tables." Compare {hash bucket}.
Remember HCF

HCF Technical Terms
HCF: /H-C-F/ n. Mnemonic for `Halt and Catch Fire', any of several undocumented and semi-mythical machine instructions with destructive side-effects, supposedly included for test purposes on several well-known architectures going as far back as the IBM 360. The MC6800 microprocessor was the first for which an HCF opcode became widely known. This instruction caused the processor to {toggle} a subset of the bus lines as rapidly as it could; in some configurations this could actually cause lines to burn up.
Explain heads down

heads down Technical Terms
heads down: [Sun] adj. Concentrating, usually so heavily and for so long that everything outside the focus area is missed. See also {hack mode} and {larval stage}, although it is not confined to fledgling hackers.
Remember heartbeat

heartbeat Technical Terms
heartbeat: n. 1. The signal emitted by a Level 2 Ethernet transceiver at the end of every packet to show that the collision-detection circuit is still connected. 2. A periodic synchronization signal used by software or hardware, such as a bus clock or a periodic interrupt. 3. The `natural' oscillation frequency of a computer's clock crystal, before frequency division down to the machine's clock rate. 4. A signal emitted at regular intervals by software to demonstrate that it is still alive. Sometimes hardware is designed to reboot the machine if it stops hearing a heartbeat. See also {breath-of-life packet}.
Expose heatseeker

heatseeker Technical Terms
heatseeker: [IBM] n. A customer who can be relied upon to always buy the latest version of an existing product (not quite the same as a member the {lunatic fringe}). A 1992 example of a heatseeker is someone who, owning a 286 PC and Windows 3.0, goes out and buys Windows 3.1 (which offers no worthwhile benefits unless you have a 386). If all customers were heatseekers, vast amounts of money could be made by just fixing the bugs in each release (n) and selling it to them as release (n+1).
Explain heavy wizardry
heavy wizardry Technical Terms
heavy wizardry: n. Code or designs that trade on a particularly intimate knowledge or experience of a particular operating system or language or complex application interface. Distinguished from {deep magic}, which trades more on arcane *theoretical* knowledge. Writing device drivers is heavy wizardry; so is interfacing to {X} (sense 2) without a toolkit. Esp. found in comments similar to "Heavy wizardry begins here ...". Compare {voodoo programming}.
Explain heavyweight

heavyweight Technical Terms
heavyweight: adj. High-overhead; {baroque}; code-intensive; featureful, but costly. Esp. used of communication protocols, language designs, and any sort of implementation in which maximum generality and/or ease of implementation has been pushed at the expense of mundane considerations such as speed, memory utilization, and startup time. {EMACS} is a heavyweight editor; {X} is an *extremely* heavyweight window system. This term isn't pejorative, but one man's heavyweight is another's {elephantine} and a third's {monstrosity}. Oppose `lightweight'. Usage: now borders on techspeak, especially in the compound `heavyweight process'.
Remember handle

handle Technical Terms
handle: [from CB slang] n. An electronic pseudonym; a `nom de guerre' intended to conceal the user's true identity. Network and BBS handles function as the same sort of simultaneous concealment and display one finds on Citizen's Band radio, from which the term was adopted. Use of grandiose handles is characteristic of {cracker}s, {weenie}s, {spod}s, and other lower forms of network life; true hackers travel on their own reputations rather than invented legendry.
Expose hand-roll

hand-roll Technical Terms
hand-roll: [from obs. mainstream slang `hand-rolled' in opposition to `ready-made', referring to cigarettes] v. To perform a normally automated software installation or configuration process {by hand}; implies that the normal process failed due to bugs in the configurator or was defeated by something exceptional in the local environment. "The worst thing about being a gateway between four different nets is having to hand-roll a new sendmail configuration every time any of them upgrades."
Expose handshaking

handshaking Technical Terms
handshaking: n. Hardware or software activity designed to start or keep two machines or programs in synchronization as they {do protocol}. Often applied to human activity; thus, a hacker might watch two people in conversation nodding their heads to indicate that they have heard each others' points and say "Oh, they're handshaking!". See also {protocol}.
Explain handwave

handwave Technical Terms
handwave: [poss. from gestures characteristic of stage magicians] 1. v. To gloss over a complex point; to distract a listener; to support a (possibly actually valid) point with blatantly faulty logic. 2. n. The act of handwaving. "Boy, what a handwave!" If someone starts a sentence with "Clearly..." or "Obviously..." or "It is self-evident that...", it is a good bet he is about to handwave (alternatively, use of these constructions in a sarcastic tone before a paraphrase of someone else's argument suggests that it is a handwave). The theory behind this term is that if you wave your hands at the right moment, the listener may be sufficiently distracted to not notice that what you have said is {bogus}. Failing that, if a listener does object, you might try to dismiss the objection with a wave of your hand. The use of this word is often accompanied by gestures: both hands up, palms forward, swinging the hands in a vertical plane pivoting at the elbows and/or shoulders (depending on the magnitude of the handwave); alternatively, holding the forearms in one position while rotating the hands at the wrist to make them flutter. In context, the gestures alone can suffice as a remark; if a speaker makes an outrageously unsupported assumption, you might simply wave your hands in this way, as an accusation, far more eloquent than words could express, that his logic is faulty.
Explain hang

hang Technical Terms
hang: v. 1. To wait for an event that will never occur. "The system is hanging because it can't read from the crashed drive". See {wedged}, {hung}. 2. To wait for some event to occur; to hang around until something happens. "The program displays a menu and then hangs until you type a character." Compare {block}. 3. To attach a peripheral device, esp. in the construction `hang off': "We're going to hang another tape drive off the file server." Implies a device attached with cables, rather than something that is strictly inside the machine's chassis.
Expose Hanlon's Razor

Hanlon's Razor Technical Terms
Hanlon's Razor: prov. A corollary of {Finagle's Law}, similar to Occam's Razor, that reads "Never attribute to malice that which can be adequately explained by stupidity." The derivation of the common title Hanlon's Razor is unknown; a similar epigram has been attributed to William James. Quoted here because it seems to be a particular favorite of hackers, often showing up in {fortune cookie} files and the login banners of BBS systems and commercial networks. This probably reflects the hacker's daily experience of environments created by well-intentioned but short-sighted people.
Expose happily

happily Technical Terms
happily: adv. Of software, used to emphasize that a program is unaware of some important fact about its environment, either because it has been fooled into believing a lie, or because it doesn't care. The sense of `happy' here is not that of elation, but rather that of blissful ignorance. "The program continues to run, happily unaware that its output is going to /dev/null."
Discover haque

haque Technical Terms
haque: /hak/ [USENET] n. Variant spelling of {hack}, used only for the noun form and connoting an {elegant} hack.
Remember hardcoded

hardcoded Technical Terms
hardcoded: adj. 1. Said of data inserted directly into a program, where it cannot be easily modified, as opposed to data in some {profile}, resource (see {de-rezz} sense 2), or environment variable that a {user} or hacker can easily modify. 2. In C, this is esp. applied to use of a literal instead of a `#define' macro (see {magic number}).
Explain hardwarily
hardwarily Technical Terms
hardwarily: /hard-weir'*-lee/ adv. In a way pertaining to hardware. "The system is hardwarily unreliable." The adjective `hardwary' is *not* traditionally used, though it has recently been reported from the U.K. See {softwarily}.
Explain Hackintosh
Hackintosh Technical Terms
Hackintosh: n. 1. An Apple Lisa that has been hacked into emulating a Macintosh (also called a `Mac XL'). 2. A Macintosh assembled from parts theoretically belonging to different models in the line.
Remember hackish
hackish Technical Terms
hackish: /hak'ish/ adj. (also {hackishness} n.) 1. Said of something that is or involves a hack. 2. Of or pertaining to hackers or the hacker subculture. See also {true-hacker}.
Expose hackishness

hackishness Technical Terms
hackishness: n. The quality of being or involving a hack. This term is considered mildly silly. Syn. {hackitude}.
Remember hackitude

hackitude Technical Terms
hackitude: n. Syn. {hackishness}; this word is considered sillier.
Remember hair
hair Technical Terms
hair: [back-formation from {hairy}] n. The complications that make something hairy. "Decoding {TECO} commands requires a certain amount of hair." Often seen in the phrase `infinite hair', which connotes extreme complexity. Also in `hairiferous' (tending to promote hair growth): "GNUMACS elisp encourages lusers to write complex editing modes." "Yeah, it's pretty hairiferous all right." (or just: "Hair squared!")
Expose hairy

hairy Technical Terms
hairy: adj. 1. Annoyingly complicated. "{DWIM} is incredibly hairy." 2. Incomprehensible. "{DWIM} is incredibly hairy." 3. Of people, high-powered, authoritative, rare, expert, and/or incomprehensible. Hard to explain except in context: "He knows this hairy lawyer who says there's nothing to worry about." See also {hirsute}. The adjective `long-haired' is well-attested to have been in slang use among scientists and engineers during the early 1950s; it was equivalent to modern `hairy' senses 1 and 2, and was very likely ancestral to the hackish use. In fact the noun `long-hair' was at the time used to describe a person satisfying sense 3. Both senses probably passed out of use when long hair was adopted as a signature trait by the 1960s counterculture, leaving hackish `hairy' as a sort of stunted mutant relic.
Discover HAKMEM

HAKMEM Technical Terms
HAKMEM: /hak'mem/ n. MIT AI Memo 239 (February 1972). A legendary collection of neat mathematical and programming hacks contributed by many people at MIT and elsewhere. (The title of the memo really is "HAKMEM", which is a 6-letterism for `hacks memo'.) Some of them are very useful techniques, powerful theorems, or interesting unsolved problems, but most fall into the category of mathematical and computer trivia. Here is a sampling of the entries (with authors), slightly paraphrased: Item 41 (Gene Salamin): There are exactly 23,000 prime numbers less than 2^18. Item 46 (Rich Schroeppel): The most *probable* suit distribution in bridge hands is 4-4-3-2, as compared to 4-3-3-3, which is the most *evenly* distributed. This is because the world likes to have unequal numbers: a thermodynamic effect saying things will not be in the state of lowest energy, but in the state of lowest disordered energy. Item 81 (Rich Schroeppel): Count the magic squares of order 5 (that is, all the 5-by-5 arrangements of the numbers from 1 to 25 such that all rows, columns, and diagonals add up to the same number). There are about 320 million, not counting those that differ only by rotation and reflection. Item 154 (Bill Gosper): The myth that any given programming language is machine independent is easily exploded by computing the sum of powers of 2. If the result loops with period = 1 with sign +, you are on a sign-magnitude machine. If the result loops with period = 1 at -1, you are on a twos-complement machine. If the result loops with period greater than 1, including the beginning, you are on a ones-complement machine. If the result loops with period greater than 1, not including the beginning, your machine isn't binary --- the pattern should tell you the base. If you run out of memory, you are on a string or bignum system. If arithmetic overflow is a fatal error, some fascist pig with a read-only mind is trying to enforce machine independence. But the very ability to trap overflow is machine dependent. By this strategy, consider the universe, or, more precisely, algebra: Let X = the sum of many powers of 2 = ...111111. Now add X to itself: X + X = ...111110 Thus, 2X = X - 1, so X = -1. Therefore algebra is run on a machine (the universe) that is two's-complement. Item 174 (Bill Gosper and Stuart Nelson): 21963283741 is the only number such that if you represent it on the {PDP-10} as both an integer and a floating-point number, the bit patterns of the two representations are identical. Item 176 (Gosper): The "banana phenomenon" was encountered when processing a character string by taking the last 3 letters typed out, searching for a random occurrence of that sequence in the text, taking the letter following that occurrence, typing it out, and iterating. This ensures that every 4-letter string output occurs in the original. The program typed BANANANANANANANA.... We note an ambiguity in the phrase, "the Nth occurrence of." In one sense, there are five 00's in 0000000000; in another, there are nine. The editing program TECO finds five. Thus it finds only the first ANA in BANANA, and is thus obligated to type N next. By Murphy's Law, there is but one NAN, thus forcing A, and thus a loop. An option to find overlapped instances would be useful, although it would require backing up N - 1 characters before seeking the next N-character string. Note: This last item refers to a {Dissociated Press} implementation. See also {banana problem}. HAKMEM also contains some rather more complicated mathematical and technical items, but these examples show some of its fun flavor.
Explain hakspek

hakspek Technical Terms
hakspek: /hak'speek/ n. A shorthand method of spelling found on many British academic bulletin boards and {talker system}s. Syllables and whole words in a sentence are replaced by single ASCII characters the names of which are phonetically similar or equivalent, while multiple letters are usually dropped. Hence, `for' becomes `4'; `two', `too', and `to' become `2'; `ck' becomes `k'. "Before I see you tomorrow" becomes "b4 i c u 2moro". First appeared in London about 1986, and was probably caused by the slowness of available talker systems, which operated on archaic machines with outdated operating systems and no standard methods of communication. Has become rarer since. See also {talk mode}.
Discover hamster
hamster Technical Terms
hamster: n. 1. [Fairchild] A particularly slick little piece of code that does one thing well; a small, self-contained hack. The image is of a hamster happily spinning its exercise wheel. 2. A tailless mouse; that is, one with an infrared link to a receiver on the machine, as opposed to the conventional cable. 3. [UK] Any item of hardware made by Amstrad, a company famous for its cheap plastic PC-almost-compatibles.
Remember hand-hacking

hand-hacking Technical Terms
hand-hacking: n. 1. The practice of translating {hot spot}s from an {HLL} into hand-tuned assembler, as opposed to trying to coerce the compiler into generating better code. Both the term and the practice are becoming uncommon. See {tune}, {bum}, {by hand}; syn. with v. {cruft}. 2. More generally, manual construction or patching of data sets that would normally be generated by a translation utility and interpreted by another program, and aren't really designed to be read or modified by humans.
Discover hack together

hack together Technical Terms
hack together: vt. To throw something together so it will work. Unlike `kluge together' or {cruft together}, this does not necessarily have negative connotations.
Remember hack up

hack up Technical Terms
hack up: vt. To {hack}, but generally implies that the result is a hack in sense 1 (a quick hack). Contrast this with {hack on}. To `hack up on' implies a {quick-and-dirty} modification to an existing system. Contrast {hacked up}; compare {kluge up}, {monkey up}, {cruft together}.
Explain hack value

hack value Technical Terms
hack value: n. Often adduced as the reason or motivation for expending effort toward a seemingly useless goal, the point being that the accomplished goal is a hack. For example, MacLISP had features for reading and printing Roman numerals, which were installed purely for hack value. See {display hack} for one method of computing hack value, but this cannot really be explained. As a great artist once said of jazz: "If you hafta ask, you ain't never goin' to find out."
Discover hack-and-slay

hack-and-slay Technical Terms
hack-and-slay: v. (also `hack-and-slash') 1. To play a {MUD} or go mudding, especially with the intention of {berserking} for pleasure. 2. To undertake an all-night programming/hacking session, interspersed with stints of mudding as a change of pace. This term arose on the British academic network amongst students who worked nights and logged onto Essex University's MUDs during public-access hours (2 A.M. to 7 A.M.). Usually more mudding than work was done in these sessions.
Explain hacked off

hacked off Technical Terms
hacked off: [analogous to `pissed off'] adj. Said of system administrators who have become annoyed, upset, or touchy owing to suspicions that their sites have been or are going to be victimized by crackers, or used for inappropriate, technically illegal, or even overtly criminal activities. For example, having unreadable files in your home directory called `worm', `lockpick', or `goroot' would probably be an effective (as well as impressively obvious and stupid) way to get your sysadmin hacked off at you.
Remember hacked up

hacked up Technical Terms
hacked up: adj. Sufficiently patched, kluged, and tweaked that the surgical scars are beginning to crowd out normal tissue (compare {critical mass}). Not all programs that are hacked become `hacked up'; if modifications are done with some eye to coherence and continued maintainability, the software may emerge better for the experience. Contrast {hack up}.
Expose hacker

hacker Technical Terms
hacker: [originally, someone who makes furniture with an axe] n. 1. A person who enjoys exploring the details of programmable systems and how to stretch their capabilities, as opposed to most users, who prefer to learn only the minimum necessary. 2. One who programs enthusiastically (even obsessively) or who enjoys programming rather than just theorizing about programming. 3. A person capable of appreciating {hack value}. 4. A person who is good at programming quickly. 5. An expert at a particular program, or one who frequently does work using it or on it; as in `a UNIX hacker'. (Definitions 1 through 5 are correlated, and people who fit them congregate.) 6. An expert or enthusiast of any kind. One might be an astronomy hacker, for example. 7. One who enjoys the intellectual challenge of creatively overcoming or circumventing limitations. 8. [deprecated] A malicious meddler who tries to discover sensitive information by poking around. Hence `password hacker', `network hacker'. See {cracker}. The term `hacker' also tends to connote membership in the global community defined by the net (see {network, the} and {Internet address}). It also implies that the person described is seen to subscribe to some version of the hacker ethic (see {hacker ethic, the}. It is better to be described as a hacker by others than to describe oneself that way. Hackers consider themselves something of an elite (a meritocracy based on ability), though one to which new members are gladly welcome. There is thus a certain ego satisfaction to be had in identifying yourself as a hacker (but if you claim to be one and are not, you'll quickly be labeled {bogus}). See also {wannabee}.
Explain hacker ethic

hacker ethic Technical Terms
hacker ethic: : n. 1. The belief that information-sharing is a powerful positive good, and that it is an ethical duty of hackers to share their expertise by writing free software and facilitating access to information and to computing resources wherever possible. 2. The belief that system-cracking for fun and exploration is ethically OK as long as the cracker commits no theft, vandalism, or breach of confidentiality. Both of these normative ethical principles are widely, but by no means universally) accepted among hackers. Most hackers subscribe to the hacker ethic in sense 1, and many act on it by writing and giving away free software. A few go further and assert that *all* information should be free and *any* proprietary control of it is bad; this is the philosophy behind the {GNU} project. Sense 2 is more controversial: some people consider the act of cracking itself to be unethical, like breaking and entering. But this principle at least moderates the behavior of people who see themselves as `benign' crackers (see also {samurai}). On this view, it is one of the highest forms of hackerly courtesy to (a) break into a system, and then (b) explain to the sysop, preferably by email from a {superuser} account, exactly how it was done and how the hole can be plugged --- acting as an unpaid (and unsolicited) {tiger team}. The most reliable manifestation of either version of the hacker ethic is that almost all hackers are actively willing to share technical tricks, software, and (where possible) computing resources with other hackers. Huge cooperative networks such as {USENET}, {Fidonet} and Internet (see {Internet address}) can function without central control because of this trait; they both rely on and reinforce a sense of community that may be hackerdom's most valuable intangible asset.
Discover hacking run

hacking run Technical Terms
hacking run: [analogy with `bombing run' or `speed run'] n. A hack session extended long outside normal working times, especially one longer than 12 hours. May cause you to `change phase the hard way' (see {phase}).
Remember Hacking X for Y

Hacking X for Y Technical Terms
Hacking X for Y: [ITS] n. The information ITS made publicly available about each user (the INQUIR record) was a sort of form in which the user could fill out fields. On display, two of these fields were combined into a project description of the form "Hacking X for Y" (e.g., `"Hacking perceptrons for Minsky"'). This form of description became traditional and has since been carried over to other systems with more general facilities for self-advertisement (such as UNIX {plan file}s).
Explain gurfle

gurfle Technical Terms
gurfle: /ger'fl/ interj. An expression of shocked disbelief. "He said we have to recode this thing in FORTRAN by next week. Gurfle!" Compare {weeble}.
Remember guru

guru Technical Terms
guru: n. [UNIX] An expert. Implies not only {wizard} skill but also a history of being a knowledge resource for others. Less often, used (with a qualifier) for other experts on other systems, as in `VMS guru'. See {source of all good bits}.
Remember guru meditation

guru meditation Technical Terms
guru meditation: n. Amiga equivalent of `panic' in UNIX (sometimes just called a `guru' or `guru event'). When the system crashes, a cryptic message "GURU MEDITATION #XXXXXXXX.YYYYYYYY" appears, indicating what the problem was. An Amiga guru can figure things out from the numbers. Generally a {guru} event must be followed by a {Vulcan nerve pinch}. This term is (no surprise) an in-joke from the earliest days of the Amiga. There used to be a device called a `Joyboard' which was basically a plastic board built onto on a joystick-like device; it was sold with a skiing game cartridge for the Atari game machine. It is said that whenever the prototype OS crashed, the system programmer responsible would calm down by concentrating on a solution while sitting cross-legged on a Joyboard trying to keep the board in balance. This position resembled that of a meditating guru. Sadly, the joke was removed in AmigaOS 2.04.
Discover gweep

gweep Technical Terms
gweep: /gweep/ [WPI] 1. v. To {hack}, usually at night. At WPI, from 1977 onwards, this often indicated that the speaker could be found at the College Computing Center punching cards or crashing the {PDP-10} or, later, the DEC-20; the term has survived the demise of those technologies, however, and is still live in late 1991. "I'm going to go gweep for a while. See you in the morning" "I gweep from 8pm till 3am during the week." 2. n. One who habitually gweeps in sense 1; a {hacker}. "He's a hard-core gweep, mumbles code in his sleep."
Discover h

h Technical Terms
h: [from SF fandom] infix. A method of `marking' common words, i.e., calling attention to the fact that they are being used in a nonstandard, ironic, or humorous way. Originated in the fannish catchphrase "Bheer is the One True Ghod!" from decades ago. H-infix marking of `Ghod' and other words spread into the 1960s counterculture via underground comix, and into early hackerdom either from the counterculture or from SF fandom (the three overlapped heavily at the time). More recently, the h infix has become an expected feature of benchmark names (Dhrystone, Rhealstone, etc.); this is prob. patterning on the original Whetstone (the name of a laboratory) but influenced by the fannish/counterculture h infix.
Remember ha ha only serious

ha ha only serious Technical Terms
ha ha only serious: [from SF fandom, orig. as mutation of HHOK, `Ha Ha Only Kidding'] A phrase (often seen abbreviated as HHOS) that aptly captures the flavor of much hacker discourse. Applied especially to parodies, absurdities, and ironic jokes that are both intended and perceived to contain a possibly disquieting amount of truth, or truths that are constructed on in-joke and self-parody. This lexicon contains many examples of ha-ha-only-serious in both form and content. Indeed, the entirety of hacker culture is often perceived as ha-ha-only-serious by hackers themselves; to take it either too lightly or too seriously marks a person as an outsider, a {wannabee}, or in {larval stage}. For further enlightenment on this subject, consult any Zen master. See also {{Humor, Hacker}}, and {AI koans}.
Discover hack

hack Technical Terms
hack: 1. n. Originally, a quick job that produces what is needed, but not well. 2. n. An incredibly good, and perhaps very time-consuming, piece of work that produces exactly what is needed. 3. vt. To bear emotionally or physically. "I can't hack this heat!" 4. vt. To work on something (typically a program). In an immediate sense: "What are you doing?" "I'm hacking TECO." In a general (time-extended) sense: "What do you do around here?" "I hack TECO." More generally, "I hack `foo'" is roughly equivalent to "`foo' is my major interest (or project)". "I hack solid-state physics." 5. vt. To pull a prank on. See sense 2 and {hacker} (sense 5). 6. vi. To interact with a computer in a playful and exploratory rather than goal-directed way. "Whatcha up to?" "Oh, just hacking." 7. n. Short for {hacker}. 8. See {nethack}. 9. [MIT] v. To explore the basements, roof ledges, and steam tunnels of a large, institutional building, to the dismay of Physical Plant workers and (since this is usually performed at educational institutions) the Campus Police. This activity has been found to be eerily similar to playing adventure games such as Dungeons and Dragons and {Zork}. See also {vadding}. Constructions on this term abound. They include `happy hacking' (a farewell), `how's hacking?' (a friendly greeting among hackers) and `hack, hack' (a fairly content-free but friendly comment, often used as a temporary farewell). For more on this totipotent term see "{The Meaning of `Hack'}". See also {neat hack}, {real hack}.
Expose hack attack

hack attack Technical Terms
hack attack: [poss. by analogy with `Big Mac Attack' from ads for the McDonald's fast-food chain; the variant `big hack attack' is reported] n. Nearly synonymous with {hacking run}, though the latter more strongly implies an all-nighter.
Remember hack mode

hack mode Technical Terms
hack mode: n. 1. What one is in when hacking, of course. 2. More specifically, a Zen-like state of total focus on The Problem that may be achieved when one is hacking (this is why every good hacker is part mystic). Ability to enter such concentration at will correlates strongly with wizardliness; it is one of the most important skills learned during {larval stage}. Sometimes amplified as `deep hack mode'. Being yanked out of hack mode (see {priority interrupt}) may be experienced as a physical shock, and the sensation of being in it is more than a little habituating. The intensity of this experience is probably by itself sufficient explanation for the existence of hackers, and explains why many resist being promoted out of positions where they can code. See also {cyberspace} (sense 2). Some aspects of hackish etiquette will appear quite odd to an observer unaware of the high value placed on hack mode. For example, if someone appears at your door, it is perfectly okay to hold up a hand (without turning one's eyes away from the screen) to avoid being interrupted. One may read, type, and interact with the computer for quite some time before further acknowledging the other's presence (of course, he or she is reciprocally free to leave without a word). The understanding is that you might be in {hack mode} with a lot of delicate {state} (sense 2) in your head, and you dare not {swap} that context out until you have reached a good point to pause. See also {juggling eggs}.
Discover hack on

hack on Technical Terms
hack on: vt. To {hack}; implies that the subject is some pre-existing hunk of code that one is evolving, as opposed to something one might {hack up}.

